2022ciscn 初赛分区赛部分wp
初赛
ez_usb
tshark过滤提取出不同src的usb流量
tshark -r ez_usb.pcapng -Y "usb.src==\"2.8.1\"" -T fields -e usb.capdata > usb.dat |
WangYihang/UsbKeyboardDataHacker: USB键盘流量包取证工具 , 用于恢复用户的击键信息 (github.com) 的脚本稍微修改一下
#!/usr/bin/env python |
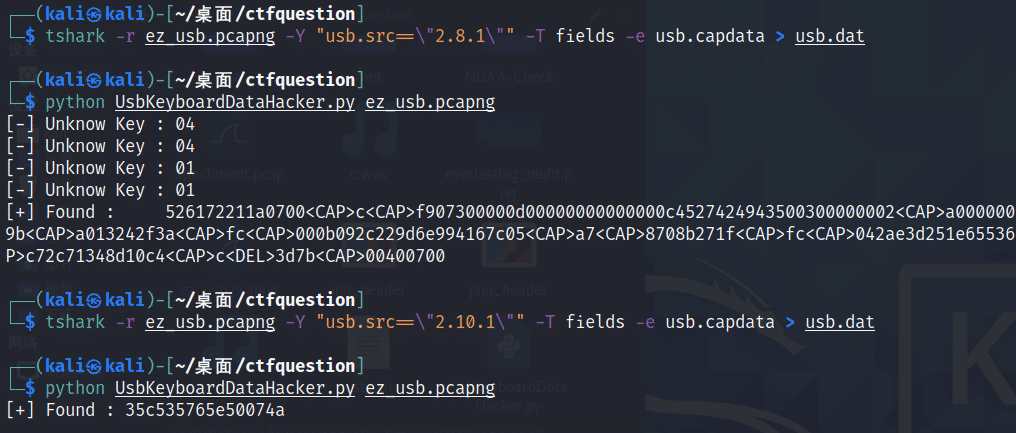
得到
526172211a0700cf907300000d00000000000000c4527424943500300000002a00000002b9f9b0530778b5541d33080020000000666c61672e747874b9ba013242f3afc000b092c229d6e994167c05a78708b271ffc042ae3d251e65536f9ada87c77406b67d0e6316684766a86e844dc81aa2c72c71348d10c43d7b00400700
和
35c535765e50074a
第一个可以转化为rar压缩包,第二个是密码,得到flag
everlasting_night
图片尾有额外数据 FB3EFCE4CEAC2F5445C7AE17E3E969AB
md5解密得到 ohhWh04m1
stegsolve查看注意到Alpha 2时右下角有东西,data extract查看Alpha 2通道,得到 f78dcd383f1b574b
考虑lsb隐写,cloacked-pixel
python lsb.py extract everlasting_night.png flag.zip f78dcd383f1b574b |
得到flag.zip
用ohhWh04m1解压缩,得到一张格式上是png但是无法查看的图片
用gmip原始数据导入,得到flag
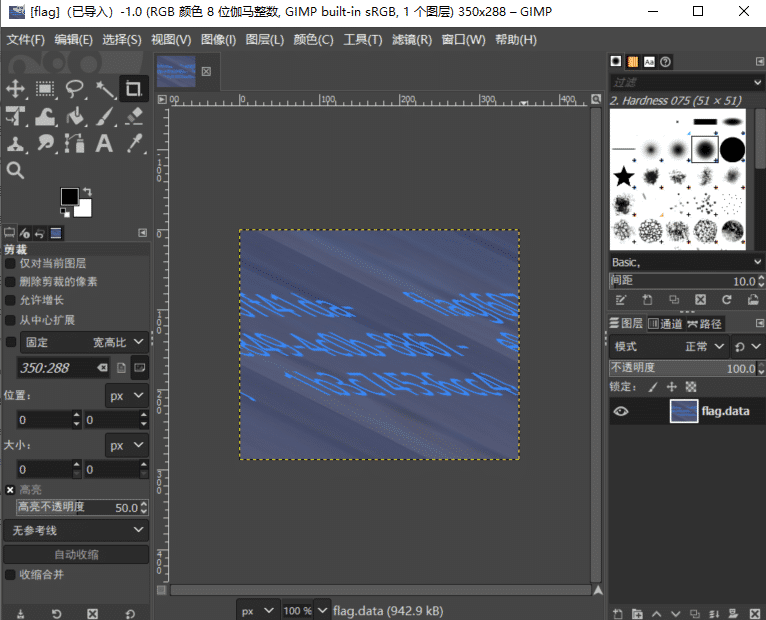
babydisk(复现)
取证大师打开vmdk文件,发现一个音频和一个SECRET文件。
john爆破deepsound,得到密码 feedback
SECRET文件是TrueCrypt加密文件,用上面的密码VeraCrypt挂载,拿到spiral文件,意思是螺旋
spiral文件大小是7569字节,刚好是87的平方,可以凑一个矩阵
螺旋矩阵,python实现_幽幽山村一小生的博客-CSDN博客_python螺旋矩阵
import binascii |
得到
ohhhhhhf5-410f3f969bI696}6-a-1eb59ge1-4d3{f9af107
分成7x7
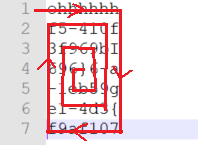
按螺旋法读取即可得到flag
华东北分区赛
pikalang
stegsolve查看,三个0通道都有隐藏数据,勾选提取出来
cGkgcGkgcGkgcGkgcGkgcGkgcGkgcGkgcGkgcGkgcGlrYSBwaXBpIHBpIHBpcGkgcGkgcGkgcGkgcGlwaSBwaSBwaSBwaSBwaSBwaSBwaSBwaSBwaXBpIHBpIHBpIHBpIHBpIHBpIHBpIHBpIHBpIHBpIHBpIHBpY2h1IHBpY2h1IHBpY2h1IHBpY2h1IGthIGNodSBwaXBpIHBpcGkgcGlwaSBwaXBpIHBpIHBpIHBpa2FjaHUgcGkgcGkgcGkgcGkgcGkgcGkgcGlrYWNodSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBwaWthY2h1IHBpIHBpIHBpIHBpIHBpIHBpIHBpa2FjaHUgcGkgcGkgcGkgcGkgcGkgcGkgcGkgcGkgcGkgcGkgcGkgcGkgcGkgcGkgcGkgcGkgcGkgcGkgcGkgcGkgcGlrYWNodSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBrYSBwaWthY2h1IHBpY2h1IGthIGthIGthIGthIGthIGthIGthIGthIGthIGthIGthIGthIGthIGthIGthIGthIHBpa2FjaHUga2Ega2Ega2Ega2EgcGlrYWNodSBwaSBwaSBwaWthY2h1IHBpIHBpIHBpa2FjaHUgcGlwaSBwaWthY2h1IHBpY2h1IGthIGthIGthIGthIGthIHBpa2FjaHUgcGlwaSBwaSBwaSBwaWthY2h1IHBpY2h1IHBpIHBpIHBpIHBpa2FjaHUga2Ega2Ega2EgcGlrYWNodSBwaXBpIHBpa2FjaHUga2Ega2Ega2Ega2Ega2EgcGlrYWNodSBwaSBwaSBwaSBwaWthY2h1IHBpY2h1IGthIHBpa2FjaHUgcGkgcGkgcGkgcGlrYWNodSBrYSBwaWthY2h1IHBpcGkgcGkgcGlrYWNodSBwaWthY2h1IHBpY2h1IHBpIHBpa2FjaHUga2Ega2Ega2EgcGlrYWNodSBwaSBwaWthY2h1IHBpIHBpIHBpIHBpIHBpIHBpIHBpIHBpIHBpa2FjaHUga2Ega2Ega2Ega2Ega2Ega2EgcGlrYWNodSBwaXBpIHBpIHBpa2FjaHUgcGljaHUgcGlrYWNodSBwaXBpIGthIGthIGthIGthIGthIHBpa2FjaHUgcGkgcGkgcGkgcGkgcGkgcGlrYWNodSBwaWNodSBrYSBrYSBwaWthY2h1IHBpIHBpIHBpIHBpIHBpa2FjaHUga2EgcGlrYWNodSBrYSBrYSBrYSBrYSBwaWthY2h1IHBpIHBpIHBpIHBpIHBpIHBpIHBpIHBpIHBpa2FjaHUgcGlwaSBwaSBwaSBwaSBwaSBwaSBwaSBwaSBwaSBwaSBwaSBwaSBwaSBwaSBwaSBwaSBwaSBwaSBwaSBwaSBwaSBwaSBwaSBwaSBwaWthY2h1IA==
base64解码
pi pi pi pi pi pi pi pi pi pi pika pipi pi pipi pi pi pi pipi pi pi pi pi pi pi pi pipi pi pi pi pi pi pi pi pi pi pi pichu pichu pichu pichu ka chu pipi pipi pipi pipi pi pi pikachu pi pi pi pi pi pi pikachu ka ka ka ka ka ka ka ka ka ka ka pikachu pi pi pi pi pi pi pikachu pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pikachu ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka pikachu pichu ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka pikachu ka ka ka ka pikachu pi pi pikachu pi pi pikachu pipi pikachu pichu ka ka ka ka ka pikachu pipi pi pi pikachu pichu pi pi pi pikachu ka ka ka pikachu pipi pikachu ka ka ka ka ka pikachu pi pi pi pikachu pichu ka pikachu pi pi pi pikachu ka pikachu pipi pi pikachu pikachu pichu pi pikachu ka ka ka pikachu pi pikachu pi pi pi pi pi pi pi pi pikachu ka ka ka ka ka ka pikachu pipi pi pikachu pichu pikachu pipi ka ka ka ka ka pikachu pi pi pi pi pi pikachu pichu ka ka pikachu pi pi pi pi pikachu ka pikachu ka ka ka ka pikachu pi pi pi pi pi pi pi pi pikachu pipi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pikachu
搜索得知皮卡丘编程语言
Pikalang Programming Language - Online Pikachu Decoder, Translator (dcode.fr)
在线网站解密得到flag
snowberg
zsteg查看发现”b1,rgb,lsb,xy”通道有zip压缩包,提取出来
压缩包里分别是1.txt,2.txt,3.txt,key.txt
其中前三个文件都是6字节,尝试crc爆破
theonlypwner/crc32: CRC32 tools: reverse, undo/rewind, and calculate hashes (github.co
得到 y0u_f0und_th1s_k3y,解压得到key.txt:63f0c7380cc3a35
010 editor打开图片,很多chunk块的crc报错,把所有报错的crc值提取出来得到
553246736447566b58312b6d4d78726330596b4776546142306333413945674657766a67687161386a2b4a34767330534f38713471584f2b4f664b4f4969682b7a4f774c426536344c32334d637562555465316478413d3d
hex 转 base64
U2FsdGVkX1+mMxrc0YkGvTaB0c3A9EgFWvjghqa8j+J4vs0SO8q4qXO+OfKOIih+zOwLBe64L23McubUTe1dxA==
aes解密 在线AES加密 | AES解密 - 在线工具 (sojson.com) key就是之前得到
得到flag
内存中的secret
逆天题,偏旁当密码,到现在也没想明白🤢
waiting to update……
good lock
waiting to update……
Folder’s revenge
waiting to update……
嫌疑人的秘密
waiting to update……
Android emulator Forensics
waiting to update……







